The modern battlefield has a new extension—cyberspace! And the modern battlefield is no longer confined to simple geographies of land masses, airspace, oceans, valleys and mountains. Better (more destructive) bombs, missiles, rockets, guns, and fighter aircraft, weren’t enough for us feisty humans. Just as the global economy has blurred once sharply defined geographical and economic boundaries, our technologies have similarly clouded the scope, locations, and players in an international conflict. As the events in Ukraine continue to evolve, and regardless of the outcome, it is clear that there are no cyber sidelines to the conflict. This means every business, every organization, regardless of its national origin, distance from the physical fray, or perceived role (or uninvolved nature by any rational assessment) may be subject to cyberattack, directly or indirectly. An emergency $32.5 billion funding request the White House sent to Congress tells the story. That request also includes: $28 million to bolster the FBI’s response to “cyber threats stemming from the Russia threat and war on Ukraine.” Physical war is a summation of specific engagements. So is cyberwar.
- The Lapus$ hacking group is reported to have recently leaked proprietary information about Samsung and Nvidia
- Agence France-Presse reported that France’s Space Command, was hit with a cyberattack
- German officials say a cyberattack that targeted Viasat caused its customers to lose their Internet on Feb. 24, and also prevented thousands of German wind turbines from connecting to the internet, blocking operators from controlling the turbines remotely.
Companies large and small can easily become collateral damage; disruptive, hurtful, but aside and apart from direct military actions, adding to the total impact of modern military and political conflict. Past cyberattacks on Colonial Pipeline, US banks, and other national infrastructure components demonstrate the eagerness of malicious actors to disrupt normal business. These attacks are often aimed at critical infrastructure, that our own companies and families rely upon for important and often essential services. So, you may be a healthcare provider, or a small school, or a retailer; you may be in the US, or the EU or elsewhere, it really doesn’t matter. Any of us can get caught up in the action, by intent, or through unintentional activities. Our societies have grown increasingly reliant on our digital technology to function throughout our daily lives. Disruption or destruction can be deeply damaging.
There are three (3) basic vectors of cyberattack we all need to address now; those that gather information, disable or destroy data or infrastructure, and those that seek to discredit fact, authority, and purpose. Let’s look at each in a bit more detail, along with the cyber risk controls and practices to apply to reduce our vulnerability and address each threat vector.
Gathering Information
Intelligence gathering has always been an important aspect of a ground war, or even a cold war. It’s also a common first step towards launching a successful, malevolent cyberattack. There are two shades of intelligence gathering; accumulation of private information to discover vulnerabilities, gain advantage, or avoid confrontation, by copying information and transferring those copies, OR to take possession of data assets to otherwise compromise another party. Real professionals favor copying data. Since nothing is “taken”, nothing is missing, and it makes detection and determination of exactly what’s compromised harder to determine. There are many tools to aid the malicious actor in pursuing these efforts. Phishing emails have long been a part of this effort. And now, smishing—the text based alternative to phishing has become a great means of trying to cajole information, sometimes through social engineering efforts. These techniques are also used to introduce malware that can take advantage of a user’s credentials and authentication to extend the information gathering reach into all the devices in a network domain.
By the way, just how segmented and secure is your network? (More on this later.)
Destroying Credibility
Aside from data theft, discrediting facts, and truth while promoting falsehood in its place may be the most damaging and long lived threat a malicious actor of any size and sophistication may promote. There is no lack of examples of evidence that misinformation, once carefully and creatively promoted, distributed, and repeated, can and does gain traction and acceptance regardless of the strength of facts to the contrary. Take the Flat Earth believers for example, and the numerous conspiracy theories that have clear evidence to the contrary, but still foster belief. I won’t name them here, but every reader knows at least one or more clear examples. Promoting “alternative facts,” outright lies, or just misinformation that draws truth into question are frequent missions for governments and political activists seeking to manipulate public opinion, behavior, or the outcome of elections and legislation. There’re also the personal attacks where malware or ransomware takes possession of private data and threatens to publicize it unless paid a ransom of money or involuntary actions by its victim.
Destroying Assets
Pretty straightforward. Whether physical devices, critical infrastructure like pipelines or electrical grids, or internet service providers, information websites, hospital records, banks, market exchanges, or almost any data resources of importance, they are all tempting targets for malicious actors seeking to disrupt an adversary of any size. Whether through ransomware, malware, or other electronic means where one attack leads to a cascading assault upon another (no electrical power can ultimately lead to no internet, heat, healthcare, manufacturing, retail, or other activities). There have also been successful attacks on SCADA systems. Supervisory control and data acquisition (SCADA) is a system of software and hardware elements crucial for industrial organizations since they help maintain efficiency, process data for informed decisions, and communicate system issues to help mitigate downtime. SCADA systems are the backbone of many modern industries, including energy, manufacturing and transportation.
Countering The Risks Of Cyberattack
Let’s look at the controls and counter measures readily available to begin to mitigate the risks to you and your businesses in this challenging cyber environment.
Gathering Information:
There are four (4) primary control practices here you should be actively practicing. Leading the list is education and training. Effective user education is one of the best means for avoiding the risks associated with phishing and smishing attacks that most often lead to successful penetration of your infrastructure defenses. Next up, comprehensive monitoring. Employing tools to monitor efforts by brute force or other means to break into your periphery, or to access internal assets without valid credentials. These should where practical, include monitoring for unauthorized or unexpected changes to infrastructure. Coupled tightly with this are strong access and authentication controls. Also, explore your network design and device configuration. Have you created segments to require specific authorization to access assets and resources on a “need to” basis, or are your controls just a barrier to a wide open interior, sometimes called a “moat and castle” design? Segmentation can slow down or minimize the damage a successful penetration of your network may inflict. Lastly, if you have the means, data loss prevention (DLP) tools to detect the unauthorized movement of sensitive data. These systems alert monitors to efforts to extract or move protected confidential data and can be configured to take preventative action in some instances.
Destroying Credibility:
These attacks are often behavioral and emotional in substance, making them difficult to thwart using technology alone. These threats seek to discredit authority, facts, or psychologically confuse wherever they may. Certainly, pay attention to your access controls, validation and authentication practices to assure users in fact are who they present themselves to be. Where there is an opportunity, certainly filter access (at least through business provided assets) to questionable sources and locations online. As a business, you have the right to monitor and manage how your resources are used. So, monitoring tools that may block access to offensive or otherwise questionable online resources is certainly within your authority. There’s also an increased need for transparency and consistency wherever practicable. A strong, consistent track record is one of the best defenses here.
Destroying Assets:
A recent blog post discussed resiliency, and certainly it applies here. Backups may seem boring, but they are a clear, effective means to protect sensitive digital assets. So too, are alternative sources of services and goods. Do you have solutions in place, tested and ready to deploy, if you lose electrical power, cell and/or internet services, transportation, or other services vital to your business? Do you have backup generators, solar arrays, or even backup power storage (i.e., battery) options? What if one or more key suppliers or partners falls victim to attack? Will you become collateral damage or do you have alternatives ready to step in? How are you managing third party risk (TPRM)? If your work-from-home staff depend upon these or their own resources, what are your plans? The best way to address risk of destruction is to prepare for alternative resources before you need them, paying particular attention to those truly essential services first.
Where Do You Turn For Answers?
Answers reside within the findings of your risk assessments, the remediations planned, and actions underway, if they were well done, current, and accurately documented. How does your most recent assessment evaluate your readiness based upon some of the issues and recommendations noted above? Did you make use of a control framework such as NIST’s Cyber Security Framework to help you organize and assure you addressed all the control areas that comprise a comprehensive cyber risk assessment? Were results quantified, compared to past assessments and rated for criticality against your core business operations and goals? Are your assessment findings compared to your relevant audit findings, contractual and regulatory obligations? Does your risk program readily help you answer questions about your cyber preparedness, critical vulnerabilities, and areas for attention? Can you accurately estimate the resources you need and where they may most effectively be applied? Can you track and report the status of remediations already planned or underway? If not, you may be approaching this effort without a roadmap, or a dashboard to guide your efforts.
A quality GRC tool implemented and employed to support your cyber risk program would help you satisfy these requirements, give you a clear picture of where you stand, point out strengths as well as critical weaknesses, and help you manage risk effectively and economically. Their data presentation tools, data visualization and analytical, make communication of meaningful findings, presented in business context, a straightforward activity. Today there are GRC options and implementations scaled to the needs of many business sizes and scopes. Some even offer “out-of-the-box” operating functionality that requires little more than a turn key service. These can offer some real value to businesses just getting started, and may offer the ability to build upon those systems as your needs require more.
Final Thoughts
Our information lives, business, social, and personal are all more transparent and more intertwined through our shared technologies than they were in generations recently past. And, we’ve all become more dependent upon resources such as mobile devices, the internet, cellular services, and “smart” technologies that connect our homes, vehicles, workplaces, and “selves” in ways unimaginable even 15 years ago. Businesses have become just so blended, interconnected, and reliant. Third party services are more widely employed and tightly integrated. So too, are our clients and customers. The threat of disruption to these services and relationships can often lead to existential consequences. Our need for cyber diligence in times of peace as well as political upheaval are growing, and will continue to expand well past the horizons of today.
About the Author:
Simon Goldstein is an accomplished senior executive blending both technology and business expertise to formulate, impact, and achieve corporate strategies. A retired senior manager of Accenture’s IT Security and Risk Management practice, he has achieved results through the creation of customer value, business growth, and collaboration. An experienced change agent with primary experience in financial, technology, and retail industries, he’s led efforts to achieve ISO2700x certification and HIPAA compliance, as well as held credentials of CRISC, CISM, CISA.
—-
Some observations from DoubleCheck Software on Cyber Security Risk Management and Third Party Risk Management (TPRM) tools:
Using the NIST framework or your own, make sure your GRC system provides tools to assess and report on your cybersecurity risk profile, with insights into specific areas of focus for the firm or for individual areas within the firm, including a summary gap analysis and associated details.
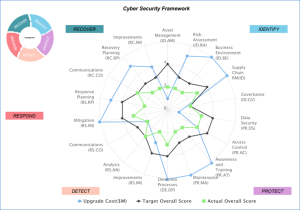
And for Third Party Risk Management (TPRM) programs, ensure that your reporting tools can provide an accurate picture, in real-time, of the status of your vendors and the risks associated with each one.

To learn more, click on Cyber Security Risk Management or Third Party Risk Management.
—

