This is the final part of a Six-Part blog series on Cyber Risk Management from guest blogger Simon Goldstein.
“If you don’t know where you are or where you are going, how will you know when you get there?” Sounds obvious enough, doesn’t it? But not very many years ago, when computerized charts and graphs became easier to produce using personal computers and laser then color inkjet printers, it was quite common to present business graphics without noting goal, optimal, or target values.
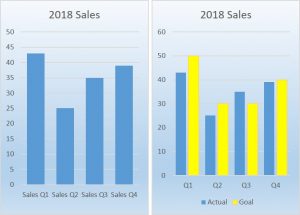

The chart on the left tells you something about sales for a period of time. The Chart on the right tells you that expectations, upon which other business decisions may have been dependent, has not been met for two quarters, and by how much. That data could raise questions, and upon further examination, offer some clue to corrective actions to be taken. So, while all were novel and pretty to look at, some were decorative, while others were actionable. Taking a patient’s temperature is useful because we have a normal healthy expectation around 98.6°F. A lot more or less indicates a problem to address.
So too, a cybersecurity risk assessment represents a measure of “where you are”. And in the case of cyber security “where you are” is a vital measure critical to your company’s ability to determine cyber risk, assess healthy practices, deficient ones, weaknesses and vulnerabilities. Done smartly, in the context of target expectations based upon risk appetite, industry norms, best practices and known threats, the assessment can point the way towards reasoned and impactful allocation of resources, material as well as operational, to close gaps and gain strength in your management of cyber risk and security. Let’s look at some specifics.
Exploring and Determining Scope
“Where does the organization start; where does it end?” Will your assessment address the enterprise or a specific subset of its current reach? This may not be so simple to draw as it seems. Consider how your company works, and where. Will mobile devices, work-at-home personal equipment, and off-enterprise assets of key 3rd party suppliers and their associates be included? Do you know with certainty what hardware is where and how it’s managed? Will portable storage devices be included? Infrastructure or cloud services? What about sunset or retired devices…how are they processed and scrubbed? Should they be included? Scope, as you can see is more than just departmental or geographical, even if you start with those designations as general determinants. Understanding the scope and boundaries of your enterprise lets you document its complexities and points of vulnerability allowing you to craft assessments to focus narrowly upon specific threats or broadly over the entire enterprise and all its activities.
Profiling the Current State
“You cannot get directions to somewhere from nowhere.” Directions presume, and depend upon some statement or understanding of a departure point. Try looking up directions to somewhere online without specifying a departure point and you’ll see clear illustration of this. Nothing useful, if anything at all will result from avoiding this step. An assessment is the specific means of determining, with some degree of precision, the answer to “where you are currently”. It illuminates, defines, examines and enables you to understand your departure point. The greater your detail in this step, the clearer your insight and direction to follow in remediation and progressive actions to strengthen your cyber security and reduce cyber risk. The assessment provides the information needed to measure the effort, resources, and time needed to strengthen cyber security practices targeting threats and vulnerabilities you know, up to the level needed to reduce residual risk to acceptable levels. Without this, it’s flying in the clouds without the benefit of controls or know how to use them—flying blind in a storm!
Planning Forward, Near Term and Far
“A journey’s endpoints define its path.” While there are always options for achievement, limitations are set at once. You won’t fly to traverse a journey of five miles, nor likely walk to cross 1000. The assessment can offer visibility into needs that require greater resources and effort, but also address significant and highly likely risks—ones your business cannot ignore. Conversely, areas in strong position to remediate risk to acceptable levels may only require maintenance and nurturing rather than significant change. Presuming you have documented a Target State, one that defines the security provisions needed to reduce risks and threat vulnerabilities to acceptable levels, you’ll be able to compare the gaps between them to determine and prioritize actions. Without the detailed awareness of the Current State afforded by the assessment, and the Target State determined by management, you do not have the information needed for a rational gap closure plan. This challenges budget planning, resource allocation, funding, and overall cyber risk management. It also leaves executive management with no actionable information or recommendations based upon fact to support direction going forward. It would call the whole program’s effectiveness and utility into question.
So Why Is A Cyber Risk Assessment Important, Really?
“It’s all about energy.” Cyber threats and attacks grow in number and sophistication, as well as subtlety, almost daily. The diversity and complexity of expanding organizations through 3rd party partnerships, shared technology resources, and flexible workforce strategies challenge authority and simple lines of control. Together they create new vulnerabilities and extend existing ones. Keeping up isn’t easy, and it requires focused attention, effort, and resources. Management needs to know what risks are inherently greatest to its business operations, reputation, assets, and resources. This extends to its suppliers, and extended partnerships, where they exist. Regulatory and contractual obligations add another layer of risk opportunity, and complexity.
Effective and efficient cyber risk management requires partnership with cyber security and the executive management team. Those partnerships are essentially fueled by accurate, current information to determine direction, evaluate action effectiveness, and assure resource allocation priorities align with risk and business practicalities. The cyber risk assessment is at once foundational, informative, and directional in its support for the information needs of risk and security stakeholders and their efforts throughout the enterprise. It’s the energy that fuels these processes, and as has often been seen throughout history, a lack of energy is something we always need to care about.
Interested in where you stand? Contact DoubleCheck about a no obligation NIST Profile Assessment!

