This is Part One of a Two-Part blog series on Cybersecurity’s impact on Audit Management, by guest blogger Simon Goldstein.
When risk professionals think about integrating enterprise resources, they often exclude or overlook audit functions, internal and external. Executive management relies upon Audit for trusted feedback into its enterprise governance efforts. Audit is a great resource of value when thoughtfully applied to risk management, and cyber risk in particular, because cyber risk extends to, and is touched by virtually everything a company does. This is the same scope as Audit, affording potentially gap-free data gathering for both programs, from different perspectives; identification, assessment and remediation, with validation through evidence and inspection. It’s a powerful, holistic combination.
Cyber-attacks and events have been and continue to be big news. They have attracted attention due to significant disruptions of some large, responsible enterprises, and government agencies, often compromising confidential identity or personal information, and costing millions to compensate and remediate damage. Such events, and their growing frequency gets boards of directors’ attention, (sometimes legislators’ too) and creates expectations and demands for secure infrastructure, accurate risk, threat, and vulnerability assessment, leading to targeted effective remediation, continued security oversight and comprehensive cyber risk management. Audit has always had the attention of these groups, and is a trusted source of validation regarding actual performance and compliance. Executives, board members, regulators and legislators have confidence in cyber risk programs vetted by audit processes where they are part of overall corporate governance.
Executives want information to direct the amount and placement of resources, understand which vulnerabilities will remain, and help determine additional actions to take. Executive governance requires monitoring the progress of remediation efforts as well as the effectiveness of controls in place to address identified risks, regulatory, and contractual obligations. Regulatory and contractual obligations are both inputs to the scope and substance of cyber risk. Both may be defined in terms of controls obligations contained within governing regulations or contractual arrangements with contractors, partners, or other 3rd party suppliers. Some regulatory frameworks, such as HIPAA, may define the obligations and controls requirements for 3rd party suppliers. Some will be specified in partnership agreements, where information sharing may extend the boundaries of confidential data handling beyond the traditional ends of a parent or primary organization. Many of these controls will address security or information handling requirements, and there is often considerable overlap between these control obligations and the ones normally found in a number of information or cyber security frameworks, including National Institute of Standards and Technology (NIST) Cyber Security Framework, ISO/IEC 27001, 2, HITECH, and COBIT 5 to name a few.
Audit, as a discipline and a business function, is often familiar with such frameworks in general, and these frameworks in specific, and knows how to evaluate, with surety, the effectiveness of controls across the blend of frameworks impacting your organization. These frameworks have different approaches and points of focus. Some are control oriented. Others, like ISO/IEC 27001, 2 and COBIT5 are process and procedure oriented. It’s common for an organization to adopt a blend of content from more than one standard. This is where a risk management software platform that can identify common controls across frameworks is particularly useful to help risk, audit, and compliance all take advantage of the leverage common controls offer. It also fosters the development and use of a common terminology or taxonomy across these disciplines for addressing risk, compliance, and security.

Audit collaboration with risk management and cyber risk is an extension of its normal operation. There’s a generally accepted view of defense in layers. From this perspective, Management oversight represents one level of defense. A second is offered by risk management practices, and Audit makes up a 3rd level of defense. Audit offers expertise at gathering data and evaluating evidence on control objectives, performance, and their current state. It is adept at pointing out where controls succeed to meet or exceed performance expectations and where they fall short. Auditors also have the skills to determine where performance and control objectives are misaligned. Audit is an organizational point where the lines otherwise separating operations from technology from security from legal and finance converge. This makes the Audit function a potentially vital tool, or information manifold, for integrating information flows to components of a cyber risk program. For example, Audit often contributes to or participates in areas of
- Internal Controls Testing
- Cyber Security Compliance Audits
- Determining/Validating Risk Assessment
- Cyber Incident Investigation
Internal Controls Testing
A framework’s foundation is built upon controls. Most risk programs organize around one or more frameworks. They provide structure to organizing and reporting findings, and to communicating about them in useful business terminology. Some of the control activities familiar to Information Technology (IT) and often applied in controlling cyber risk often include:
- Policy development and maintenance
- Intrusion detection systems deployment
- Event logging
- Periodic vulnerability scanning
- Information asset classification
- Systems hardening practices for shared enterprise resources
Policy development and update procedures run on cycles, often driven by annual review practices, regulatory, legal, or operating environmental changes requiring revision. Reviewing policy currency, status of revisions, completion and adherence to approval processes, publishing and distribution practices and communication in compliance with internal policies or external obligations are actions an audit function is well positioned to perform and report findings into the risk and compliance processes. This helps determine whether policy management is being executed as designed. It also points out if policy content is relatively current, has been approved by appropriate management, and whether the controls contained within the policy meet their intent within the current organization.
Asset classification is foundational to many security practices, and helps define operating, financial, legal, regulatory, and reputational, as well as cyber risk related to its mishandling. Audit functions can review policies, practices, and operational adherence to these throughout its scope in the enterprise. The degree and detail of security controls and handling practices, procedures, and policies for information handling, storage, transfer, sharing, and retention are often detailed and defined based upon a sensitivity or value-based scale of classification. Without a classification policy and clear guidelines for adhering to it, information such as product or process intellectual property, financial, customer, or other data may be at risk to disclosure to competitors, hostile actors seeking ransom for its return, or leave corporate functions unable to meet legal or regulatory obligations. These situations can lead to violations, fines, or litigation. They also create vulnerabilities due to indifferent or lax data handling by staff lacking sound guidance and education about data categories, as they relate to other information handling controls, policies or practices.
Intrusion detection, event logging, and vulnerability practices are all fairly standard IT practices supporting security, cyber defense and investigative practices. Comparing evidence of practice to policy and procedure are important controls to assure these efforts are in force and operating effectively as designed, according to stated procedures.
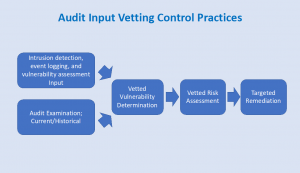
Reviews of these processes by Audit also offer an opportunity to examine whether the controls are as effective as needed, and may point to areas of fine tuning by adjusting measurement frequencies, alert thresholds, and levels of content in the information recorded. In a similar manner, audit review of system hardening practices, including related operating procedures, can offer information of the state of practices, adherence to periodic review schedules, including patch management procedures and currency of their application throughout an enterprise. Unpatched systems represent a vulnerability often cited in breaches at large companies, and attributed to overly complex or under-resourced procedures to implement them. Control reporting on the current status of patching, documented deferral procedures and approvals, and related statistics on aging and repeated deferrals are often lacking in control. This is an area where Audit can provide objective input, detailed evidence, and recommendations to improve processes, thereby constructing a bridge between cyber risk and operational data giving management actionable input to situations they might not have otherwise discovered. This will lead to positive timely direction, more efficient practices, and lower cyber risk.
For more information on a no-obligation NIST Profile Assessment, click here.
About the Author:
Simon Goldstein is an accomplished senior executive blending both technology and business expertise to formulate, impact, and achieve corporate strategies. A retired senior manager of Accenture’s IT Security and Risk Management practice, he has achieved results through creation of customer value, business growth, and collaboration. An experienced change agent with primary experience in financial, technology, and retail industries, he’s led efforts to achieve ISO2700x certification and HIPAA compliance, as well as held credentials of CRISC, CISM, CISA.

