Every CIO, CISO, and CRO has had this experience, even if only once. They have a meeting with their Board of Directors, for which they have prepared volumes of detailed factual data about the state of risk in their organization; they are confident of their preparation and their message. But, almost immediately upon beginning, the presenter is distracted and derailed by hurried questions, and impatient requests. “Give us the bottom line!” “How does this impact earnings targets this quarter?” “How are we protected from that new cyber threat I heard about on the news last night?” “Are we doing more than our peers and competitors?” “What’s our policy? Our strategy?” And so it goes. The Board wants to have a business discussion… but you prepared for a fact and process discussion about risk management.
At first glance, these different perspectives on risk seem askance of one another. But are they? Where is the intersection and integration of these two positions? How do you make important risk information meaningful in a business sense? What data do you need? What language is critical to attention and understanding? Let’s look at those relationships and see where and how to organize, analyze and translate risk information into a business context meaningful to senior executives and board members, enabling the decisions, actions, and engagement you seek to support your program and strengthen its ability to serve and protect your business.
 What Business Risks Make Sense to a Board?
What Business Risks Make Sense to a Board?
Boards care about growing and sustaining their operations, revenue, and profits. They also care about anything that might disrupt those outcomes or enhance the probability of success! So, any individual or group of risks presenting a serious threat, or exploiting a known vulnerability jeopardizing these outcomes will gather close and thoughtful attention. That sounds straightforward enough, but typical cyber threat, IT, and security risks are often expressed using different terms, metrics, values and even measurement frequencies than more traditional measures of corporate performance. So, if you want your Board’s or Executive Team’s attention, you have to address matters in their language.
Relating Business Processes to Cyber, Technology, and Performance Risks
This is really not difficult, but it does take some planning and some thoughtful analysis and arrangement of risk data. If you are fortunate, you have multiple sources for risk data available. Internal and external audits have identified controls that may not be performing as designed or may require redesign to address changes in operational practices. Regulators may have reviewed compliance and noted strengths and weaknesses. Your own internal IT function likely has performance metrics on downtime, currency of software upgrades, patch applications, phishing attempts, and systems being sunset due to old age or operating well beyond manufacturer’s support coverage, to name a few possible measures. Operations keeps its own performance metrics, and notes performance outside expected values, with corrective action plans where needed. They also have responsibility for assuring continuity of service when weather or other risks offer physical threats to facilities and staff, and as a result, reliable operations. Of course, Finance is always monitoring cash, currency rates, interest, revenues, payable and receivables against target values and performance. Marketing and Sales will pay close attention to your reputation and its impact on revenue generation performance. They also monitor competition, and other factors impacting product and service design and delivery.
How do you relate these operating risk inputs to cyber threats, IT risk, and security? You need to think in terms of “causal chains”. And to do so often requires a deep understanding of how your company works. A causal chain starts with some recognizable risk control or metric, and then relates its impact back into some aspect of business operations, based upon most likely cause/effect situations, leading to a recognizable business outcome in terms of money, resources, staffing, or operations.
For example, let’s assume your IT department notices that some of the logistics servers have fallen far behind schedule on software patching. Doing so leaves those servers vulnerable to security threats that might disable them in a way requiring restoration from backup, leading to 10-12 hours of downtime. That downtime might lead to logistics missing deliveries, product outages, and lost sales. It may also lead to contractual compliance issues tied to performance penalties. This rapidly translates into dollars lost or at least at risk. So the shorthand version is “missed patching could lead to revenue risk of $nnn,nnn.”
You can look at all your key cyber risk metrics, consider the impact of the associated threat or vulnerability to business performance, and then represent these risks and the associated remediation or risk management response in terms of core business values. Performing this analysis places cyber, IT, and security risk squarely into the context of business operations. It also provides the information and context to address the matter of not spending $100,000 to address a $10,000 risk. More importantly, this way of presenting risk information demonstrates that risk management offers value as a true business partner lending useful leadership guidance and contributing to the comprehensive efforts by the Executive Team to achieve company goals and objectives.
There are other, more specific benefits gained from this analysis of risk metrics. If you come across ones that seem to defy relevance to some business practice, ask this question about the metric: “As a result of knowing the value of this metric, for this measurement period, what action would I take?” If the answer identifies no action, question why the measure is gathered and monitored. There’s a long-standing inclination to want to “know everything”. If you need to know everything, you haven’t decided what’s truly important. And if everything is important, you don’t know the key drivers of your business. No risk program, no report, no data collection effort will solve that matter for you. You do not need to know the chemical composition of the rubber in your tires to drive your car from point to point. You do need to know if you have all-weather tires or have studs, or what their performance metrics are depending upon the weather, but knowing the chemical composition of the rubber would be of little value unless you were a curious chemist. Knowing the compression ratios of each cylinder doesn’t help you be a safe driver, either. You get the point.
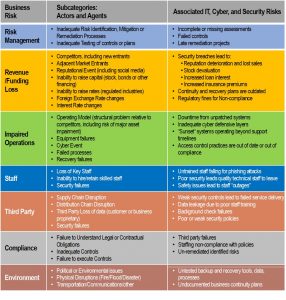
In the chart below you’ll find some categories of business risk, examples of specific business risk subcategories, and some related cyber, IT, and security risks. This is intended as a beginning guide to help your efforts to map these risks to business concerns and processes.
In the articles to follow, we’ll explore how a GRC software platform can help organize and structure the data from multiple sources necessary to perform this analysis well and generate maximum utility from your risk management practices and reporting. Then, the last article in the series will offer some guidance on how to build an effective Board level report, putting into practice the concepts and methods discussed in these Board Reporting related articles.
About the Author:
Simon Goldstein is an accomplished senior executive blending both technology and business expertise to formulate, impact, and achieve corporate strategies. A retired senior manager of Accenture’s IT Security and Risk Management practice, he has achieved results through the creation of customer value, business growth, and collaboration. An experienced change agent with primary experience in financial, technology, and retail industries, he’s led efforts to achieve ISO2700x certification and HIPAA compliance, as well as held credentials of CRISC, CISM, CISA.

