There are lessons to be learned from the Colonial Pipeline ransomware attack. Panic is not one of them—it will yield no improvement nor progress for any situation. The event does strongly highlight how much more attention we need to pay to cyber risk now than past efforts demonstrate. The details of this ransomware incident are less significant than the overarching evidence that our national infrastructure, commercial, governmental, educational, and personal all are much more vulnerable than we like to believe. Further we have a vivid example of how disruptive a cyber attack’s consequences may be and how ill prepared we are to address, protect, or recover gracefully from one. Colonial reportedly paid millions in ransom to recover its systems. And even then, not everything was recovered. That may not always be an option, nor is it ever a strategy that protects any entity from a repeat occurrence. Of course, all cyber threats are not rooted in ransomware. Some seek to acquire otherwise secured information and exploit it. Others seek to destroy their targets, and a few are designed to achieve both. For many information security and cyber risk professionals these circumstances are nothing new. What is new, and deeply disturbing, is this current demonstration of just how vulnerable we may all be to any number of cyber threats, and how unprepared we are to recover from successful ones. Let’s look at a three-step approach to answer the question “what are we going to do about this?” The simple answer is to Organize, Assess, and Act!
Organize
Random, overheated and haste-fueled reaction to these events will not yield any useful improvement nor enhance any aspect of your organization’s infrastructure, resilience or resistance to cyber threats. Be thoughtful, and get organized. Step back, array the aspects of security and cyber risk management essential to detection, protection, identification, and recovery. If you utilize a framework, bring it forward, update it if needed. If not, this is a great opportunity to bring one to bear. The NIST (National Institute of Standards and Technology) Cyber Security Framework is a good choice. And, for those who seek even more detailed and expansive control sets and guidance, NIST’s Security and Privacy Controls, 800-53, recently update to release 5, is very helpful. In past articles I’ve discussed the NIST Cyber Security Framework. Here, I’ll focus a bit upon 800-53, r5. This new release of a mainstay security controls standard has a number of enhancements over release 4. There are new control sets added to address privacy and supply chain management. For those who’ve followed discussions in past blogs regarding third party risk management (TPRM), and actively monitor supplier risk, these are particularly useful.
Some of the key features of NIST 800-53, r5 include:
- Integration of Privacy controls into the security control catalog
- Integrated Program Management controls
- New controls for Privacy, Supply Chain, and Systems Engineering
- Direct controls mappings to ISO27001 and NIST’s Cyber Security Framework
- Separation of controls from related processes to facilitate alignment with other frameworks
These are important upgrades. Let’s focus for a minute on the Supply Chain and Systems Engineering aspects. Having control sets designed and devoted to these process areas provides new structure to organizing the assessment of third-party risk (TPRM), and sharpens focus upon best practices for software application development. These are areas where malicious actors have leveraged vulnerabilities in otherwise secure target perimeters. Also, by separating control content from related processes, it’s easier to incorporate these feature sets with other relevant frameworks your company or industry may employ. This allows organizations to create custom blended sets of controls, tailored for their specific needs, to be incorporated into their risk assessment processes. The resulting comprehensive control set may offer a more thorough evaluation of risk, within infrastructure, including extensions to an enterprise perimeter created by third party interactions. This new release of 800-53 makes it much easier to map this extensive control set to the ISO27001 Information Security Standard, and the NIST’s own Cyber Security Framework. These frameworks of controls include organizing structures to enable a higher level of evaluation and reporting from a business perspective. This is essential to meaningful communication with non-technical business leadership, ensuring findings may be clearly understood by senior management.
Assess
All these frameworks and control sets offer large sets of data points to examine in assessment. The threats associated with ransomware attacks, the potential vectors that could be involved, and the vulnerabilities to address, are diverse and plentiful. The frameworks offer a means to organize and interpret assessment findings in a way meaningful to technical, operating, and executive staff. Your risk assessment program likely has organizational data on the business structures, functional, geographical, asset-based, and perhaps more.
- This is also an opportunity to take a process-based view of your risk portfolio. For example:
How are you managing access, authentication, and network security? - Is your cyber security training of staff current?
- Do you have documented, tested, validated business continuity and disaster recovery plans, roles, and processes?
- Have you inventoried and categorized your critical assets?
- Do your backups of critical systems work?
- Are your recovery time and recovery point (RTO, RPO) targets realistic?
- What due diligence are you incorporating into the validation and on-boarding process for third parties?
This last one is particularly important. While you may have strong security and user education protocols in place for your own operations and associates, those of potential service partners may be otherwise. What do you know about theirs? Do you gather such information during their onboarding? Social engineering and weaker security have created vulnerabilities in partners creating openings for threat actors to gain access into otherwise secure organizations, leading to ransomware and other cyber incidents. Your partners and providers extend your security and threat perimeter if they have any access to any assets within your domain. Your attention to this expanded horizon is more important today than ever.
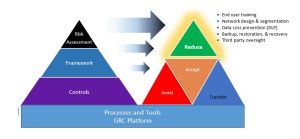
Protecting against ransomware requires all the best practices of information security. Your risk assessment should be looking at your authentication and authorization processes, network controls, security policies and associate education, asset management, and more. It’s also a great time to research recent successful ransomware attacks and how they succeeded in overcoming whatever controls were in place. How strong are those controls in your company? You’ll also want to assess your incident management, detection, backup and recovery processes. Are they understood, tested, rigorous and proven to work? They are a critical component of your resilience solution to respond to ransomware. You can see why incorporating a GRC platform into your cyber risk program provides valuable capabilities to adroitly and efficiently organize all these data, controls, frameworks, policies, and reports. A GRC is also a place to record remedial action projects and track status, manage workflow for processes like risk assessments, onboarding and assessing third parties, tracking regulatory and industry compliance, integrating audit report findings, and more.
Act
Planning, organizing, and assessment are important, but alone are not sufficient to provide strong, reliable protection from ransomware attacks. Control areas found to be weak require some strategy or action to strengthen. There are some controls that are specifically relevant to addressing risk of such attacks being successful. Specifically, look to your assessments and evaluate your strength regarding:
- End user training: All associates, at every level should have awareness training to help them identify and avoid phishing attacks, social engineering attacks, and other risky behaviors that could introduce malware into your environment
- Network design and segmentation: Sometimes referred to as zero tolerance networking, it’s all about assuring protected resources are only accessed by authorized users, that firewalled and routed segments are used to restrict wandering across an enterprise and to thwart and contain ransomware’s ability to easily compromise your entire enterprise.
- Data loss prevention (DLP): Will help monitor and report unauthorized access attempts and give you some warning about behavior that might indicate a ransomware or related event is underway
- Backup, restoration, and recovery: The software is available today to assure that this can be in place and works! There’s nothing that deflects the misery of a ransomware attack so much as the ability to restore and recover with minimal, or at least measurable data loss. Do this if you have information worth protecting.
- Third-party oversight: From evaluation through onboarding and ongoing monitoring and supervision, make certain all outside contacts or access to your network, data, or any technological resources, however apparently banal, are carefully monitored, controlled, engaged by trained and knowledgeable staff that are as aware as your own trained associates. Note: If you have a GRC, and it has a TPRM (Third Party Risk Management) component, you can use that to assess readiness, manage onboarding, vet continued compliance year-over-year, and support your regulatory and compliance reporting needs.
Ransomware may attack anyone. It’s not a risk for large institutions alone. Its purveyors are not honorable people. Paying the ransom may, and sometimes does lead to repeated incidents. Failing to pay, in the absence of the means to recover on your own, may be an existential choice. And today, ransomware as a service, RAAS, offers malicious actors who lack the technical know-how to build the attack, to simply license ransomware. Then they only need a successful phish, inattentive third party, or socially engineered event to gain access to your protected assets. Is there any question this scenario should be avoided at almost any cost? The choice is yours.
I have been openly vocal about the relative vulnerability of governmental systems, Federal, State, and Municipal. First hand, I have seen these weaknesses repeated by other major infrastructure components throughout our national enterprise, in healthcare, financial services, and many more. Policy, politics, profits, economics, and even convenience have presented challenges to our progress to make our companies, industries, government, and even our personal lives more safe, secure, and resilient. As a society and a culture, we are deeply reliant upon digital services, processes, resources, and communications. Disruption, without reasonable and diligent preparation to protect against these threats, without resilient recovery and restoration, rapidly disables our ability to function, and can threaten our safety, our financial wellbeing, our supply chains for goods services, communications, utilities, even our health. To be on guard is to be responsible, and to look away is, of itself, a threat and a risk to us all.
About the Author:
Simon Goldstein is an accomplished senior executive blending both technology and business expertise to formulate, impact, and achieve corporate strategies. A retired senior manager of Accenture’s IT Security and Risk Management practice, he has achieved results through the creation of customer value, business growth, and collaboration. An experienced change agent with primary experience in financial, technology, and retail industries, he’s led efforts to achieve ISO2700x certification and HIPAA compliance, as well as held credentials of CRISC, CISM, CISA.

