In our last blog, we explored the content and value of the New York State Department Of Financial Services 23 NYCRR 500; Cybersecurity Requirements For Financial Services Companies. In this article, we’ll explore how the application of a framework like NIST 800-53, or the NIST Cybersecurity Framework helps structure and achieve strong compliance with regulations like this one.
Let’s review what this regulation, enacted into effect in March of 2017, puts forth for financial services throughout NY State.
It begins by acknowledging the growing threat of cyber-attacks and setting forth the regulation’s intent; summarized by these points:
- Promote the protection of customer information and IT systems of regulated entities
- Proscribe regulatory minimum standards
- Allow cybersecurity programs to match the relevant risks and keep pace with technological advances.
- Require each company to assess its specific risk profile and design a program that addresses its risks in a robust fashion.
- Set Senior Management responsibility for the organization’s cybersecurity program
- Require Covered Entities to file an annual
certification confirming compliance with these regulations.
While these points set forth foundational, core
requirements and expectations, they bear a strong resemblance in language and
intent to the primary components of the NIST Cybersecurity Framework, and now
to the proposed revisions to NIST Security Standard 800-53 rev5. And, they offer common ground
between what a cyber risk professional would view as requirements for a
professionally managed cyber risk program.
They also, through the specific details of control requirements noted in
the regulation, describe minimal compliance activity. NIST 88-53 Rev4 and 5 are built around a
tiered approach to structuring information systems security, while offering 18
control families to be addressed, specifically:
- Tier 1 – The Organization
- Tier 2 – Business Processes
- Tier 3 – Information Systems
And…
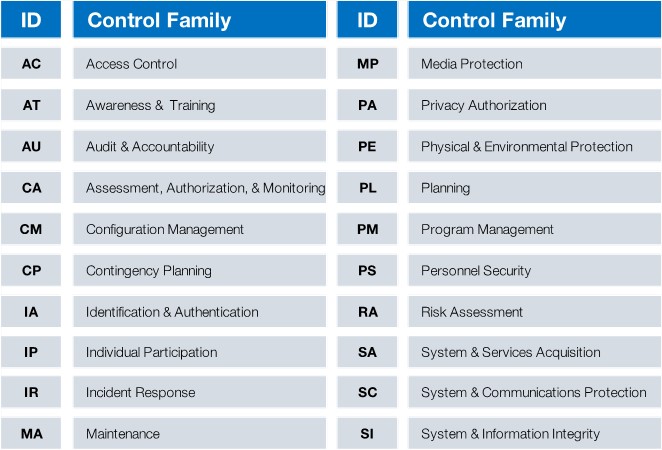
Numerous detail controls are noted within the standard utilizing this tiered approach to organization. In conjunction with this, a draft Special Publication known as the (SP) 800-37 Revision 2, and several other Federal standards combine to offer a Cyber Security Risk Framework, noting six (6) core steps:
- Step 1 – CATAGORIZE Information Systems (FIPS 199/SP 800-60) – IMPACT ASSESSMENT
- Step 2 – SELECT Security Controls (FIPS 200/SP 800-53)
- Step 3 – IMPLEMENT Security Controls (SP 800-160)
- Step 4 – ASSESS Security Controls (SP 800-53A)
- Step 5 – AUTHORIZE Information Systems (SP 800-37)
- Step 6 – MONITOR Security Controls (SP 800-137)
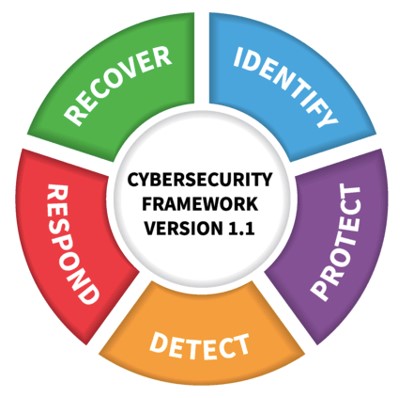
This compares well to the NIST CyberSecurity Framework and its core organizing process categories:
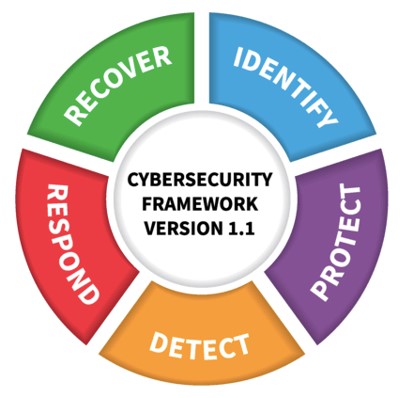
All of these standards represent efforts to place scores of detailed, process-oriented security or risk management control practices into an organized structure that makes sense to business leaders outside the professional domains of information services, technology, and cyber risk management. Business-oriented organization of these control, risk, and security practices is essential to enabling useful cross domain conversations and decisions about significance, risk, priority, resource allocation and alignment to organizational goals. It supports creation and application of a standardized, common taxonomy for these discussions, regardless of the details applicable to any single practice, or the technological know-how needed to assure their effective implementation.
Most organizations with regulatory obligations of any substance benefit from these kinds of organizing frameworks in these 10 ways by:
- providing a common structure for comparing regulatory requirements and identifying common controls.
- offering a common terminology to discuss regulatory, security, and risk management requirements and activities.
- simplifying the identification and justification for remediation activities that benefit compliance, security, and risk management, often offering efficiencies where one set of actions achieves a benefit in more than one area.
- enabling efficient and effective allocation of resources to best protect the information assets of an organization, its members, staff, and clients or customers.
- providing a common means to apply best practices for security, risk, and operations methodologies in unregulated businesses, assuring customers their information is protected in a rigorous manner.
- promoting comprehensive internal services to address risk, security, and compliance
- helping organizations sustain currency in best practices regarding risk, security, and compliance.
- recognizing and leveraging the benefits of common controls across multiple processes, disciplines, and regulatory requirements.
- comparison to peers and competitors within your vertical, whatever the dimension
- ready identification of best practices applicable to your most important concerns
Regardless of what path an organization takes, there is clearly a great deal of data that needs to be gathered, managed, organized, stored, and analyzed to support the fundamental processes of cyber risk management, information security, and regulatory compliance. Any single one would create significant need for structure and careful oversight. The presence of all three greatly increases that workload.
Some small firms will try to do this using home-grown tools. I’ve seen many examples of “Management-by-Excel” to address cyber risk, IT risk, regulatory requirement compliance, assessments, remedial action tracking, and reporting on all these fronts. Audit is another area where this malady sometimes takes root. Frankly, even the best of these “solutions” was largely undocumented, required constant attention by its creator, and offered little flexibility to address the changing requirements each of these disciplines is subject to address. It may be a great way to organize thoughts and represent portions of frameworks as they are described to fit an organization’s culture, internal taxonomy, or scope of business. And, it’s good way to organize initial thinking about these risk management practices. But such solutions are not sustainable, responsive to rapid change, nor are they readily extensible.
The advantages offered through using a framework are often best exploited through the implementation of a comprehensive GRC (Governance, Risk, and Compliance) software platform. In fact, establishment of a program founded upon a framework, even one customized through the adoption of common controls across several standards, actually makes GRC implementation more straightforward. These tools are designed to work with frameworks. They often can be delivered preconfigured with one or more standards, and some will support creation of customized ones through “cherry-picking” of common controls in conjunction with standard frameworks from other company or regulatory requirements. But that’s just to start. GRC tools are platforms for leveraging standards and other control sets to facilitate risk assessments, audits, compliance reviews, and more.
They provide tools for recording remedial activities, (both against audit findings and risk assessments of all kinds), tracking progress of related projects, correlating data from one process or operating discipline with another to cross-validate risk or audit findings, while relating all this accumulated data into meaningful status and state reports managers and executives can use to make informed decisions. GRC tools and features, properly applied, can lead to greater compliance, security, and operating effectiveness while establishing a means of directing and monitoring cost effective management for IT, operating, and cyber risk, audit, regulatory compliance, and operations. They support creation of standardized, methodical, documented, repeatable practices that can be managed with equal efficiency in centralized or distributed organizations. They scale. And they are engineered to be flexibly responsive to change. And they can be secured. Their aggregate data is often sensitive, and most support access controls appropriate to such content.
Let’s look back now to the intent of the New York State Cybersecurity Requirements For Financial Services, with some thought to how a framework and a GRC tool might specifically help:
KEY
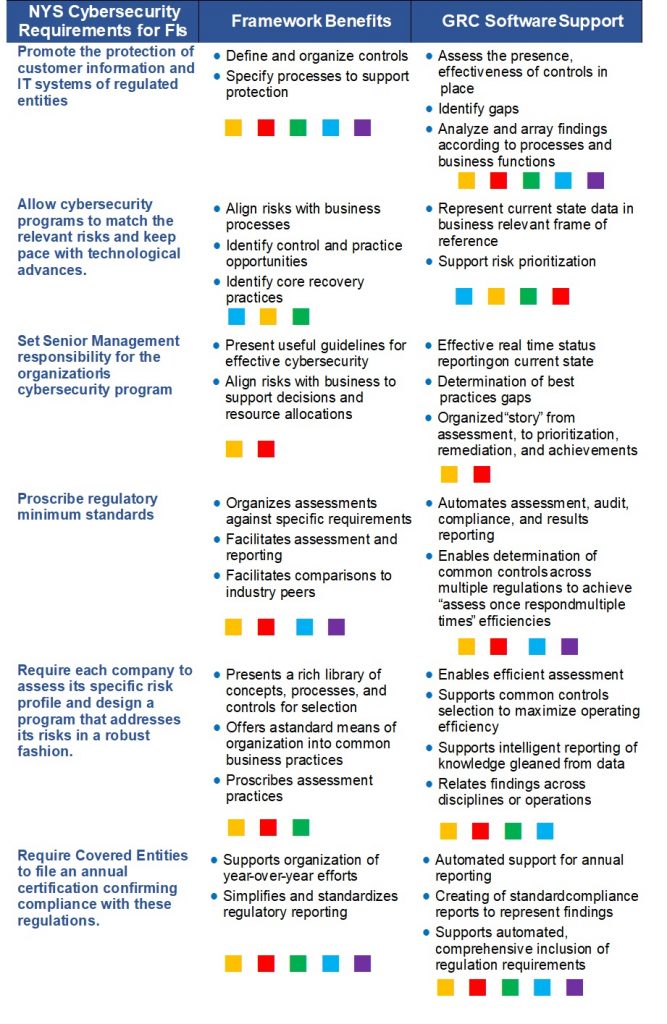
There is clearly a lot to be gained through the use of frameworks, and of GRC tools. They add considerable structure and a sense of process firmness to actions and efforts that may often seem unrelated, duplicative, and of questionable business purpose on their own. They support discipline and enable staff to function as professional process managers with regard to cyber, IT, and operational risk, while contributing those benefits to audit, compliance, regulatory review, and other areas benefiting from sound risk management practices.
Compliance with regulations is, for many industries, a practical matter that’s part of business as usual. Frameworks of controls and practices, supported through careful, thoughtful implementation of quality GRC software tools, can bring these benefits of structured professional management to this challenging aspect of contemporary business. It certainly would be of great benefit to managing compliance with the New York State Cybersecurity Requirements For Financial Services Companies.
About the Author:
Simon Goldstein is an accomplished senior executive blending both technology and business expertise to formulate, impact, and achieve corporate strategies. A retired senior manager of Accenture’s IT Security and Risk Management practice, he has achieved results through the creation of customer value, business growth, and collaboration. An experienced change agent with primary experience in financial, technology, and retail industries, he’s led efforts to achieve ISO2700x certification and HIPAA compliance, as well as held credentials of CRISC, CISM, CISA.

