This is Part One of a Six-Part blog series on Cyber Risk Management from guest blogger Simon Goldstein
In a report published by the Institute of Internal Auditors Research Foundation (IIARF) on what boards of directors need to ask about cybersecurity, it was noted that only a bit more than 14% were actively engaged in discussions on security preparedness. That study was published in 2014. By 2017, ISACA’s annual report on the state of Cybersecurity, State of Cyber Security 2017: Part 2: Current Trends in the Threat Landscape, noted that 67% of boards responded they had adequately prioritized security. Boards have gotten the message, but have they gotten the response they seek? Has yours?
Boards need to understand that cybersecurity, and therefore cyber risk, is an enterprise matter. Cyber risk extends beyond the sphere of IT management. The impact of a cyber attack and a successful breach can extend to almost any part of the organization. Cyber risks may be reputational, financial, organizational, legal, and operational. States often have specific and strict breach disclosure laws. Customer confidence in a company’s ability to detect and address a breach effectively may be critical to overall success. Breaches can clearly disrupt operational processes and generate considerable legal liability; addressing all or any of these matters can lead to significant costs. Boards care about bottom line performance and business continuity – cyber risks potentially affect both.
Your board needs to understand how cyber risk is unique. The information boundaries of modern companies are more fluid and elastic than ever before. People are enabled to work inside and outside brick and mortar locations. Mobile devices of growing diversity, often a mix of company and personally owned units based upon multiple operating systems, provide a complex challenge to controlling information data flows, presence, and overall infrastructure. It’s difficult today to predict or define the technological edges of a company’s operation. Outsourcing functions to trusted third parties adds another layer of potential diversity. Combined, these conditions create a rich opportunity base for cyber threats to present themselves, leading to a diverse, extensive risk presence. Being able to rationalize this risk in context to your actual exposure, (net of fear and distracting hype) is vital to enabling the board to make informed resource decisions.
But relating these risks to key corporate objectives is critical, and so are mitigation strategies. First, doing so places them in business context—vital to board attention. Second, doing this supports meaningful prioritization against financial, operational, legal, and reputational risks in the company’s enterprise risk register. Another important attribute of cyber risks is the need to mitigate them effectively. They cannot all be easily avoided, nor accepted, and remediation will never perfectly eliminate them. While breach insurance has become one means of deflecting some financial exposure resulting from a cyber breach, it does not fully mitigate reputational, legal, or operating impacts. Cyber risks are perpetual moving targets. It’s kind of like planning for weather. You know sooner or later it’s likely to rain, but what you plan to do about it is what’s important. Sooner or later, a cyber attack on your company will be successful. Your board needs to know what your response will be, what their role is, what outcomes to prepare to address, and how they will stay informed throughout.
Your board should expect clarity of its risk leadership. If your board asks anything of your Cyber Security and Risk Management Programs it may start by asking “who’s in charge of Cyber Security?”. But from there it’ll quickly devolve into five key questions:
- What is our company’s cyber risk and security strategy?
- What cyber risks stand in the way of achieving primary corporate goals and overall mission?
- What are we (you) doing to address these threats?
- What are our processes in the event of a cyber breach?
- Do we have the resources in place to execute our strategy?
Answering these questions directly and demonstrating well thought out processes to identify and manage cyber risk efficiently will build board confidence. To start, consider cyber risk from the business point of view. This means treating cyber risk as one more aspect or class of risk within a comprehensive risk management program. It’s important to clearly explain the cyber risk strategy and program approach to your board. That program should include all the normal practices of risk identification, mitigation, remediation, avoidance, acceptance, and transfer. Cyber risks need to be identified and evaluated; which by itself is often a considerable task making up much of associated IT security attention and resources. But cyber risk extends beyond IT, and beyond checkoff lists of process controls. People play a critical, dynamic role in executing the control and behavioral practices that help address cyber risk. So continuous education is as important as any technical tool or practice implementation.
They will want to know what Cyber Risk management will cost and why. Managing cyber risk effectively will require resources. And resources cost money. More importantly, it’s money that some might think could be better focused elsewhere. Building a sound risk management strategy, aligned with your business’s mission, scope, structure, and industry’s competitive obligations and expectations is an essential start. Upon that foundation, specific program capabilities can be defined in scope and measure appropriate to the risks your company faces. These will support informed and intelligent decisions about resource allocation and expenditures for a risk management program your board and your company can engage with confidence.
Why a GRC can help… One very effective tool for organizing and representing your program strategy, practices and current state is a comprehensive Governance Risk and Compliance (GRC) platform. These software tools let you display how you’ve organized your approach and strategy regarding cyber risk in context to business risk in other areas. This is useful to a non-technical board. They also afford simple graphics such as heat maps and reports that provide non-technical state data on the risk process specifics; what significant risks, mitigation efforts, remediation activities, associated costs and projected activities. (See Exhibit 1)
Exhibit 1

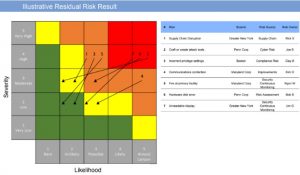
 In addition, they can incorporate established industry frameworks for cyber risk management, allowing useful comparisons to industry peers, business language taxonomies for processes and coherent communication on cyber risk issues. They help address the “why” as well as many “what” questions when defining and describing a cyber risk strategy. This information may also be leveraged to the advantage of internal audit and compliance efforts that can repurpose risk assessment and remediation findings to address issues and reporting requirements in those areas. This represents a demonstrable efficiency in data usage and could lead to realized cost savings.
In addition, they can incorporate established industry frameworks for cyber risk management, allowing useful comparisons to industry peers, business language taxonomies for processes and coherent communication on cyber risk issues. They help address the “why” as well as many “what” questions when defining and describing a cyber risk strategy. This information may also be leveraged to the advantage of internal audit and compliance efforts that can repurpose risk assessment and remediation findings to address issues and reporting requirements in those areas. This represents a demonstrable efficiency in data usage and could lead to realized cost savings.
Boards thrive on actionable, timely, accurate information. If your cyber risk program is built upon a strategy and programs designed and executed to address a dynamic cyber risk environment while generating such information, you will be well down the road to preparedness for effective cyber risk management.
About the Author:
Simon Goldstein is an accomplished senior executive blending both technology and business expertise to formulate, impact, and achieve corporate strategies. A retired senior manager of Accenture’s IT Security and Risk Management practice, he has achieved results through creation of customer value, business growth, and collaboration. An experienced change agent with primary experience in financial, technology, and retail industries, he’s led efforts to achieve ISO2700x certification and HIPAA compliance, as well as held credentials of CRISC, CISM, CISA.

